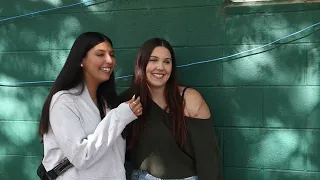Saclink access risks safety
Image: Saclink access risks safety:Rachel Josue, left, and Tiffany Carpoff use the wireless Internet in the fireplace lounge in the Union. Christina Cowan/State Hornet:
March 16, 2005
This semester, users of the campus wireless and open jack network at Sacramento State have a new, but risky way, to log into the network using SacLink for authentication.
The method increases compatibility with operating systems and Internet-compatible devices, but provides no encryption for wireless transmission and makes it easier for others to access students& data.
David Hill, director for University Computing and Communication Services, said the first wireless access points were placed around the campus in 2001.
At the time, wireless encryption methods were still in their infancy. Wired Equivalent Privacy was the first security protocol for providing encryption for wireless networks.
The early attempt at security made it easy to decrypt wireless data.
Carl Oakes, University network support for UCCS, said this was the main reason for choosing the Virtual Private Network, or VPN client, for accessing the campus network. Not only would the VPN client use students& and faculty SacLink names and passwords for login, but the client also encrypts the transmitted data, making it extremely difficult for anyone to intercept and read the information.
&With the university&s introduction of wireless networking, VPN was used
for authentication because it was relatively easy to setup and configure, and it was the best way to guarantee the security of data traveling over the wireless network,& Hill said.
While the VPN client worked great for most users, some students had problems downloading, installing and configuring the free client, available on the Sac State Web site.
Apple Macintosh users with Operating System 9 and lower and people with personal Internet-accessing devices had to purchase a client in order to access the network.
That&s why SacLink network authentication was introduced this semester, to provide an easy, client-free way to access the campus network. However, this came at the expense of data encryption.
Julio Gomez, a mechanical engineering major, uses SacLink for accessing the campus network because he has problems trying to use the VPN client.
&As long as I can use the Internet (is what matters), but I would prefer (using VPN) because it is more secure,& Gomez said.
Melissa Gomez is less concerned about wireless encryption. Although she &loves& using the wireless network, she said she uses it more for entertainment purposes and is not worried about her information being sent without security. She uses SacLink for authentication, and has not heard about the VPN client.
&I have 5,000 anti-virus definitions,& she said. &Of course (I will continue to use SacLink).&
&Because VPN encrypts user data at the user&s workstation and it remains encrypted until it reaches the university&s secured, wired infrastructure, there&s no danger that eavesdroppers on a wireless network will obtain usable information,& Hill said.
UCCS does not hide the unencryption danger from students. The &General Information& link on the SacLink network authentication Web site states that the only way to encrypt all packets sent wirelessly is with the VPN client.
&VPN requires a client to perform the encryption, so some users have resisted its use,& Hill said. &The university has provided an alternate authentication mechanism that does not require the installation of a client, but VPN is still recommended because it provides a secure connection.&
For more information about the wireless network, visit the UCCS Web site at www.csus.edu/uccs.